In the past I’ve owned VPS instances so that they can be used as proxies to setup in-country applications. For instance, some country Ministry of IT don’t like their servers managed from another country. So, the quick solution is to buy a cheap OpenVZ node from a provider advertising at lowendbox.com or ask a local IT guy to give me SSH access into his machine and setup OpenVPN server. Someone else wanted to setup the same thing that I do, so I thought I’d write this blog entry.
Server Side
The instructions are for Debian or Ubuntu or Linux Mint or similar based distros
1. Install OpenVPN
# apt-get install openvpn
2. Prepare key generation
# mkdir /etc/openvpn/easy-rsa
# cp /usr/share/doc/openvpn/examples/easy-rsa/2.0/* /etc/openvpn/easy-rsa
3. Editing vars
# cd /etc/openvpn/easy-rsa
# nano vars
Change the variables with whatever info you'd like to create the user info (KEY_SIZE is for the encryption complexity, using 2048 should be more than fine)
KEY_SIZE=2048
KEY_COUNTRY="NO"
KEY_PROVINCE="NO"
KEY_CITY="Oslo"
KEY_ORG="UiO"
KEY_EMAIL="saptarsp@test.in"
# source ./vars
4. Generating the Certificate Authority (CA)
# ./clean-all
# ./build-ca
5. Generating the Server keys - (with server name as dhisServer)
# ./build-key-server dhisServer
6. Generate the Diffie Hellman Key Exchange parameters
# ./build-dh
7. Create a client key (with client name as sunny)
# ./build-key sunny
8. Generate the HMAC code (so, that we can use TLS/SSL login without passwords)
# openvpn --genkey --secret /root/easy-rsa/keys/ta.key
9. Copy the generated keys into a keys folder
# mkdir -p /etc/openvpn/keys
# cp -pv /root/easy-rsa/keys/{ca.{crt,key},dhisServer.{crt,key},ta.key,dh2048.pem} /etc/openvpn/keys/
10. Edit the OpenVPN server configuration. Remove everything and add the following (or make changes)
# nano /etc/openvpn/server.conf
port 1194
proto udp
dev tun
ca keys/ca.crt
cert keys/server.crt
key keys/server.key # This file should be kept secret
dh keys/dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp" #all clients to redirect their default network gateway through the VPN
push "dhcp-option DNS 208.67.222.222" #OpenDNS servers
push "dhcp-option DNS 208.67.220.220"
keepalive 10 120
tls-auth keys/ta.key 0 # This file is secret
comp-lzo
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
verb 3
11. Enable IP forwarding on the server
# echo 1 > /proc/sys/net/ipv4/ip_forward
12. Forward all network traffic through NAT masquerade (Change this to eth0 to venet0 for OpenVZ or VPS nodes)
# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
13. Restart OpenVPN service
# service openvpn restart
Client Side
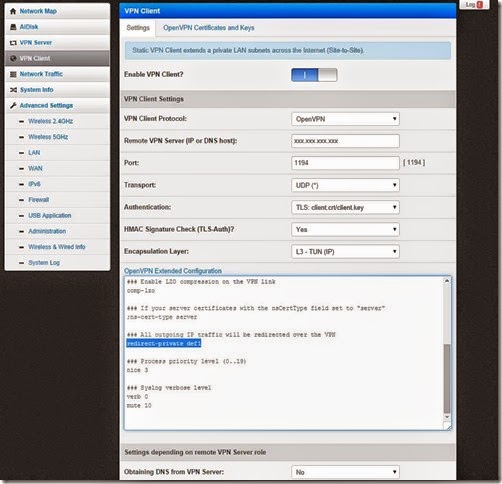
On the client side, you don’t have to do much. If you want your entire office to access through this VPN, then you should install ddwrt or another router firmware (Asus N56U Padavan’s) which has an OpenVPN client. Below is a screenshot of Padavan’s firmware OpenVPN client. Note the important extended configuration – redirect-private def1 (All outgoing IP traffic with be redirected through VPN)
If you are using Windows and want to connect, try the OpenVPN-GUI. A pretty simple, but useful client to connect to OpenVPN servers. Remember to down the one with TAP driver, so you can seamlessly get all traffic to flow through the VPN connection. After the installation is done, copy the ca.crt, sunny.crt, sunny.key and ta.key files that were generated on the server in C:\Program Files\OpenVPN\config . You can email or use WinSCP to transfer the files to the client machine. Then create a sunny.ovpn file in the same folder with the following content
# C:\Program Files\OpenVPN\config\sunny.ovpn
client
remote xxx.xxx.xxx.xxx (replace this with your server IP)
port 1194
proto udp
dev tun
dev-type tun
ns-cert-type server
reneg-sec 86400
tls-auth ta.key 1
auth-retry interact
comp-lzo yes
verb 3
ca ca.crt
cert sunny.crt
key sunny.key
management 127.0.0.1 1194
management-hold
management-query-passwords
auth-retry interact
That should be all that is required. Once you start the OpenVPN GUI, you will see a system tray icon with right-click displaying connect or if you have multiple .ovpn files then choice on which one to connect to.




 shock, but is more disappointment for me. I have been a user of Opera for at least a decade now. Although I use Chrome and Firefox for a many things, Opera has remained installed and upgraded because every new release has something innovative in it.
shock, but is more disappointment for me. I have been a user of Opera for at least a decade now. Although I use Chrome and Firefox for a many things, Opera has remained installed and upgraded because every new release has something innovative in it.